When we talk about Malware, we have to add another motivation to the risks: Lust.
This week, we have another round of malware which rides on the desire of email recipients to see Britney Spears naked. The first example is a fairly standard reminder that most anti-virus products do not detect most malware during the first few days of their attack.
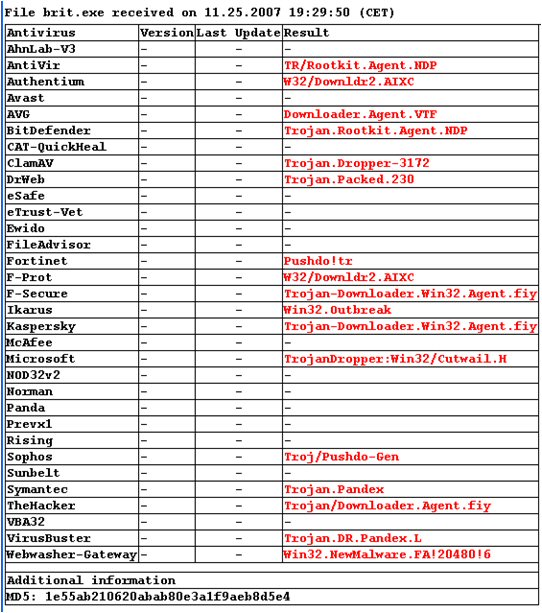
In this example, email recipients are told that the attachment to the email contains a "New Britney naked video". What the attached zip file actually contains is a file called "brit.exe", which, of course, turns the infected machine into a bot. Does anti-virus detect it? 53% of AV engines detect it at this time:
The second set of spam uses an assortment of "Britney" subject lines, including:
Britney showed it again!
which connects to a variety of sites with several paths to infection.
Several of the sites linked to from the emails, including: velart.net, blurcolombia.com, agrisanterre.com, which had been modified to include an "iframe" which pulled additional code from "meoryprof.info".
The second one I looked at linked to the website of the "Associação Nacional de Pesquisa e Pós-Graduação em Psicologia". On that page, there is a crazy bit of encoded Javascript at the top. When it is decoded, one finds that it links to two sites:
(CAUTION: THESE ARE BAD SITES! DO NOT VISIT!)
http://ramoneymayker.info/
http://spl.vip-ddos.org/
Nope. Nothing suspicious about THOSE names. "VIP Distributed Denial of Service dot org?" I wonder what happens when that box infects a PC?
The owner of "vip-ddos.org" also owns "botnet.cc". Gee. He must have been counting on his encryption preventing us from seeing those names. (AGAIN, don't visit. Even going to the homepage loads malware from certain Malaysian computers.... VIP-DDOS is actually also the name of a popular Chinese attack tool.
So what does it take to become infected by a Drive By Downloader? The temporary temptation to click on a link in an email promising a new Britney picture.






0 comments:
Post a Comment